i have reproduced it manually by POST method and got error result code ( i have attached the screenshot), on the other hand , i found it was blocked by WAF while it scanned by penetrator (based on WAF log - Screenshot attached)
The reflection of a user input in the output, especially when the output is a html form, should always be considered as a vulnerability and fixed. The solution is not reflect the user input in any part of the html sent back to the user after the POST.
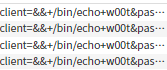
When you send a POST form with the same parameters shown in the vulnerability output,
&password=1&zLoginField=1&loginOp=login
the result is a form which contains
<form method="post" name="loginForm" action="/?+%2fbin%2fecho+w00t=&zLoginField=1"
Changing the attack parameters to something malicious, can bring to a possible code execution when the form is POSTed again.
Comments
0 comments
Please sign in to leave a comment.